加入Windows Active Directory 管理帳號,可以使用Kerberos方式驗證,這章看一下會產生什麼EventLog
https://en.wikipedia.org/wiki/Kerberos_(protocol)
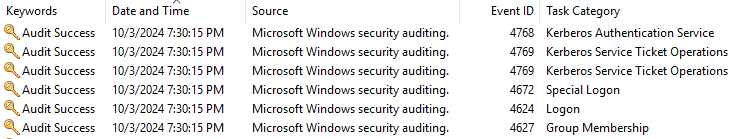
4768 A Kerberos authentication ticket (TGT) was requested.
(1)請求TGT票證的帳戶
(2)TGT請求傳送到的 Kerberos域中的服務名稱
(3)請求的電腦的IP
(4)Encryption types 0x12:AES256-CTS-HMAC-SHA1-96,
Pre-Authentication types 2, 標準密碼身份驗證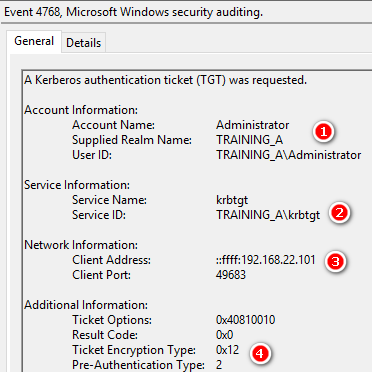
4769 A Kerberos service ticket was requested.
與4768一樣看法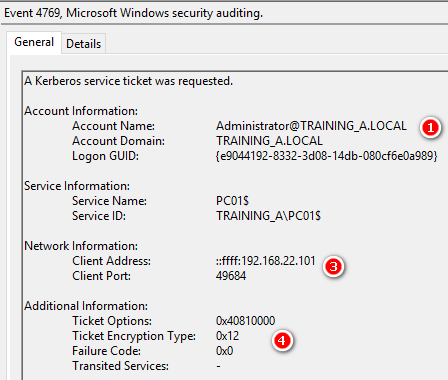
4672 Special privileges assigned to new logon
指派給新登入的敏感權限清單
4624 An account was successfully logged on
LogonType 3 從網路登入此電腦的使用者或電腦
Detailed Authentication Information 使用Kerberos方式驗證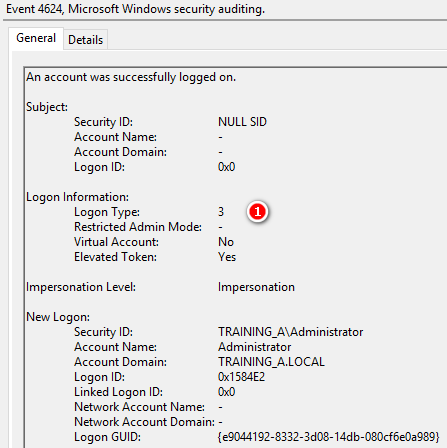
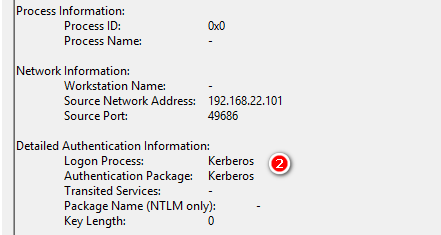
4627 Group membership information
帳號加入那些群組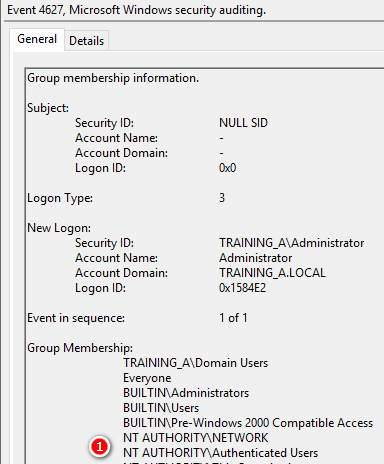
4648 A logon was attempted using explicit credentials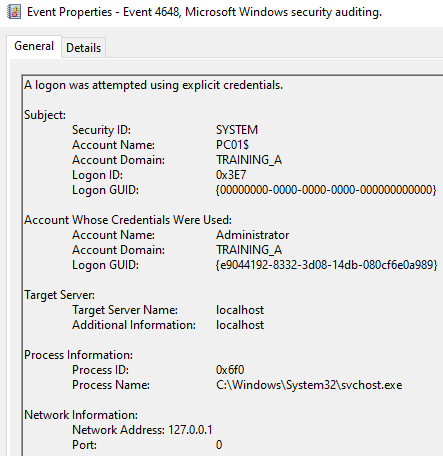
4624 An account was successfully logged on
LogonType 2 使用者登入這台電腦
Client這邊顯示是Negotiate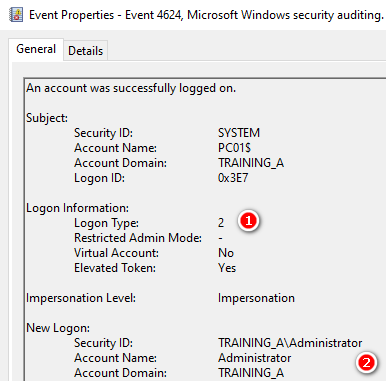
4627 Group membership information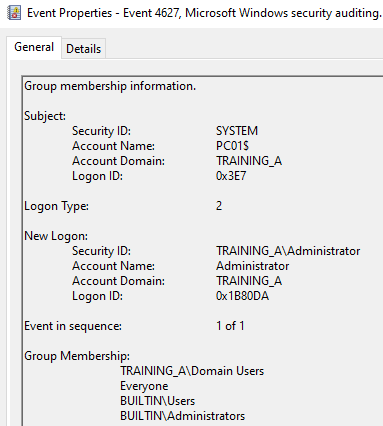
4672 Special privileges assigned to new logon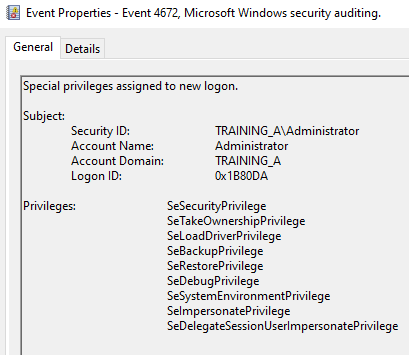
單純從4625事件看不出是連線問題
0XC000006D – 對於關鍵帳戶或服務帳戶,「這可能是由於錯誤的使用者名稱或驗證資訊」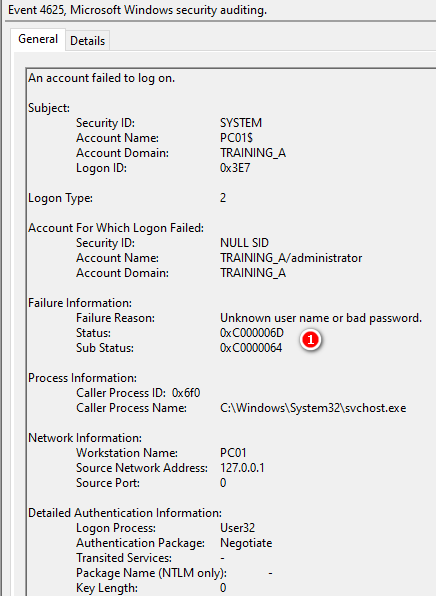
5156 The Windows Filtering Platform has permitted a connection
53/TCP,UDP DNS(域名服務系統)
88/TCP Kerberos - 認證代理
389/TCP,UDP 輕型目錄訪問協定 LDAP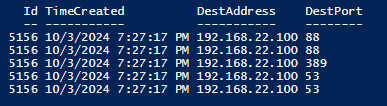
Get-WinEvent -FilterXml '
<QueryList>
<Query Id="0" Path="Security">
<Select Path="Security">
*[
System[
(EventID=5158 or EventID=5156) and
TimeCreated[@SystemTime>="2024-10-03T11:27:17.000Z" and @SystemTime<="2024-10-03T11:27:17.999Z"]
]
and EventData[
Data[@Name="DestAddress"] = "192.168.22.100"
]
]
</Select>
</Query>
</QueryList>
' |
Select-Object Id, TimeCreated,
@{Name="DestAddress"; Expression={$_.Properties[5].Value}},
@{Name="DestPort"; Expression={$_.Properties[6].Value}}
AD Security - [Day29] 一起來學 AD 安全吧!: 整理 Credential Request 相關手法與該監控的 Event ID
https://ithelp.ithome.com.tw/articles/10308756
